Babel Enterprise
System hardening evaluation
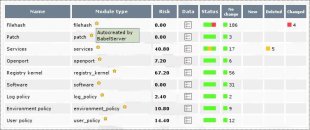
Babel Enterprise is a systems auditing tool. Babel Enterprise performs a security level check of the machine, or hardening. The check consists of a number of auditing tests that obtain a snap of the security status of each machine. The result is a security index of the system that is given after each execution.
Babel Enterprise is a non-intrusive tool, meaning that it does not make any changes in the system at all. It simply takes note of what is not working properly and reports it to the user. .
Babel Enterprise has being designed to manage security on many different systems, different technologies and versions, and different issues and requirements. It is a distributed management system, multi-user, that allows redundant installation in all its critical components.
Each change occurring in the system can be watched and marked automatically each time a new audit policy is executed. Users can add, delete or modify existing elements to see exactly if the system works better or worse and why. Babel Enterprise uses a pragmatic approach, evaluating those aspects of the system the represent a security risk and that can be improved with the intervention of an administrator.
Babel Enterprise is an extraordinarily versatile tool that contains all the information necessary to be adapted easily to any technical requirements.
Babel Enterprise has a version of its agent for each of the latest Microsoft operating systems, Windows 2003 and Windows XP, and the main Unix system: Solaris 10, AIX 5.x, SUSE GNU/Linux 9 ES and Ubuntu Dapper, although they can be easily adapted to different versions and other UNIX OSs (such as BDS or HP-UX )
Babel Enterprise currently has modules for auditing many different aspects of system security. These are some examples of currently implemented audit modules:
- Service minimization.
- Centralized file hashing.
- Anomalous SUID0 executable detection.
- File permissions checker.
- Password strenght tests.
- Generic registry lookup (Windows)
- Remote services configuration.
- Audit for Kernel networking and security parameters.
- Apache2 configuration auditing
- User accounts auditing
- Root environment audit
- UID0 users detection.
- Centralized patch management.
- Centralized software inventory.
- Listening ports auditing.
- Inetd / Xinetd minimization.
Babel Enterprise
System hardening evaluation

Babel Enterprise is a systems auditing tool. Babel Enterprise performs a security level check of the machine, or hardening. The check consists of a number of auditing tests that obtain a snap of the security status of each machine. The result is a security index of the system that is given after each execution.
Babel Enterprise is a non-intrusive tool, meaning that it does not make any changes in the system at all. It simply takes note of what is not working properly and reports it to the user. .
Babel Enterprise has being designed to manage security on many different systems, different technologies and versions, and different issues and requirements. It is a distributed management system, multi-user, that allows redundant installation in all its critical components.
Each change occurring in the system can be watched and marked automatically each time a new audit policy is executed. Users can add, delete or modify existing elements to see exactly if the system works better or worse and why. Babel Enterprise uses a pragmatic approach, evaluating those aspects of the system the represent a security risk and that can be improved with the intervention of an administrator.
Babel Enterprise is an extraordinarily versatile tool that contains all the information necessary to be adapted easily to any technical requirements.
Babel Enterprise has a version of its agent for each of the latest Microsoft operating systems, Windows 2003 and Windows XP, and the main Unix system: Solaris 10, AIX 5.x, SUSE GNU/Linux 9 ES and Ubuntu Dapper, although they can be easily adapted to different versions and other UNIX OSs (such as BDS or HP-UX )
Babel Enterprise currently has modules for auditing many different aspects of system security. These are some examples of currently implemented audit modules:
- Service minimization.
- Centralized file hashing.
- Anomalous SUID0 executable detection.
- File permissions checker.
- Password strenght tests.
- Generic registry lookup (Windows)
- Remote services configuration.
- Audit for Kernel networking and security parameters.
- Apache2 configuration auditing
- User accounts auditing
- Root environment audit
- UID0 users detection.
- Centralized patch management.
- Centralized software inventory.
- Listening ports auditing.
- Inetd / Xinetd minimization.









